This is the second in a series of guest blogs from significant voices in the industry with something to say about LTE. This time we hear from Ben Volkow, VP Product of Product Development for F5 Traffix.
This is the second in a series of guest blogs from significant voices in the industry with something to say about LTE. This time we hear from Ben Volkow, VP Product of Product Development for F5 Traffix.
I know this is becoming my mantra, and may therefore sound a bit repetitive but I’ll say it again. One of the main success factors of LTE roll out and services is dependent on the quality of an operator’s Diameter Signalling Solutions. Allow me to explain.
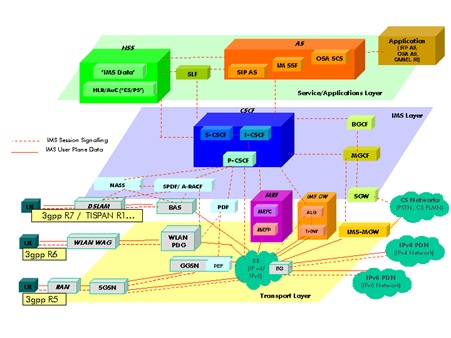
LTE devices, including smartphones, tablets, dongles, and all of the other connected devices generate an unprecedented volume of signalling, sometimes even more than 100 times the amount of signalling we are used to experiencing in legacy networks. Signalling is the network’s internal communication system, and the language that signalling “speaks” in LTE is an IP-based stream control transmission protocol called Diameter. It plays a connecting and routing function among LTE networks and inside the network between the different network nodes.
Diameter exists everywhere in the network, for example, among enabling elements for policy management and enforcement, billing and charging, authentication, mobility management, and roaming services.
LTE was designed on the drawing board as a Greenfield technology, replacing existing legacy 2G, 2.5G, and 3G networks and building new 4G networks from scratch. Keep in mind however, that in telecoms there tends to be more evolution than revolution. So, in practice, next-generation elements are deployed side-by-side with existing legacy network functionalities. This two-generation hybrid complicates the network by filling it up with a patchwork of technologies, interfaces, and protocols. And this complication—referred to as network fragmentation—is extremely costly if not handled properly. Minimally, it requires connectivity between the LTE interfaces, protocols, and elements, as well as connectivity between the new and legacy components.
In addition, there is the huge task of simplifying this network spaghetti, and only a robust Diameter Signalling router can succeed here.
Now back to the LTE devices. Many are designed with power-saving mechanisms to preserve battery life. However, simply touching the device catalyzes signalling. Many consumers leave several applications open, such as mobile games and social networking sites—and this causes constant, massive signalling.
The “always-on” state of LTE devices are constantly pinging the network with signalling, creating a volume of signalling messages that are greater than ever experienced by a network.
The high level buzz around LTE speaks about an enhanced multimedia, personalised, and interactive experience. More specifically, LTE is expected to deliver advanced services and charging schemes such as family data plans, tiered data plans, video optimisation, and faster speeds of mobile data. Each one of these improvements involves complicated “back-office” support in the network.
Each LTE service comes with a complex navigation route among network elements like PCRFs (policy charging & rules function) that tells the network what level of data plan has been purchased by the subscriber. OCS (online charging system) elements are needed to serve prepaid customers, and BSS (business support systems) elements that are connected to data centres across vast geographic areas and require signalling to deliver the billing charges to the correct data centre.
In short, it is the Diameter Signalling router (more commonly known as DRA) that ensures that the correct information about the right subscriber is transmitted to the designated server in the network.
So, my take on the state of the LTE market is that we have witnessed a great beginning. And from our perspective, there are two types of service providers. The first is the service provider who plans for signalling routing and gateway solutions from the beginning, and the second is the service provider who doesn’t add it to the plan and ultimately experiences pain due to signalling surges and overloads. This second type of service provider quickly realises its mistakes and rushes to deploy Diameter routers and load balancers to ensure network reliability and maximum performance.
In both scenarios, LTE networks experience a bombardment of signalling at unprecedented levels. This signalling must be managed, or it will upset network performance significantly or bring network operations to a halt.
The LTE World Summit is taking place on the 23-24 May 2012 CCIB, Barcelona, Spain. Click here to register your interest.